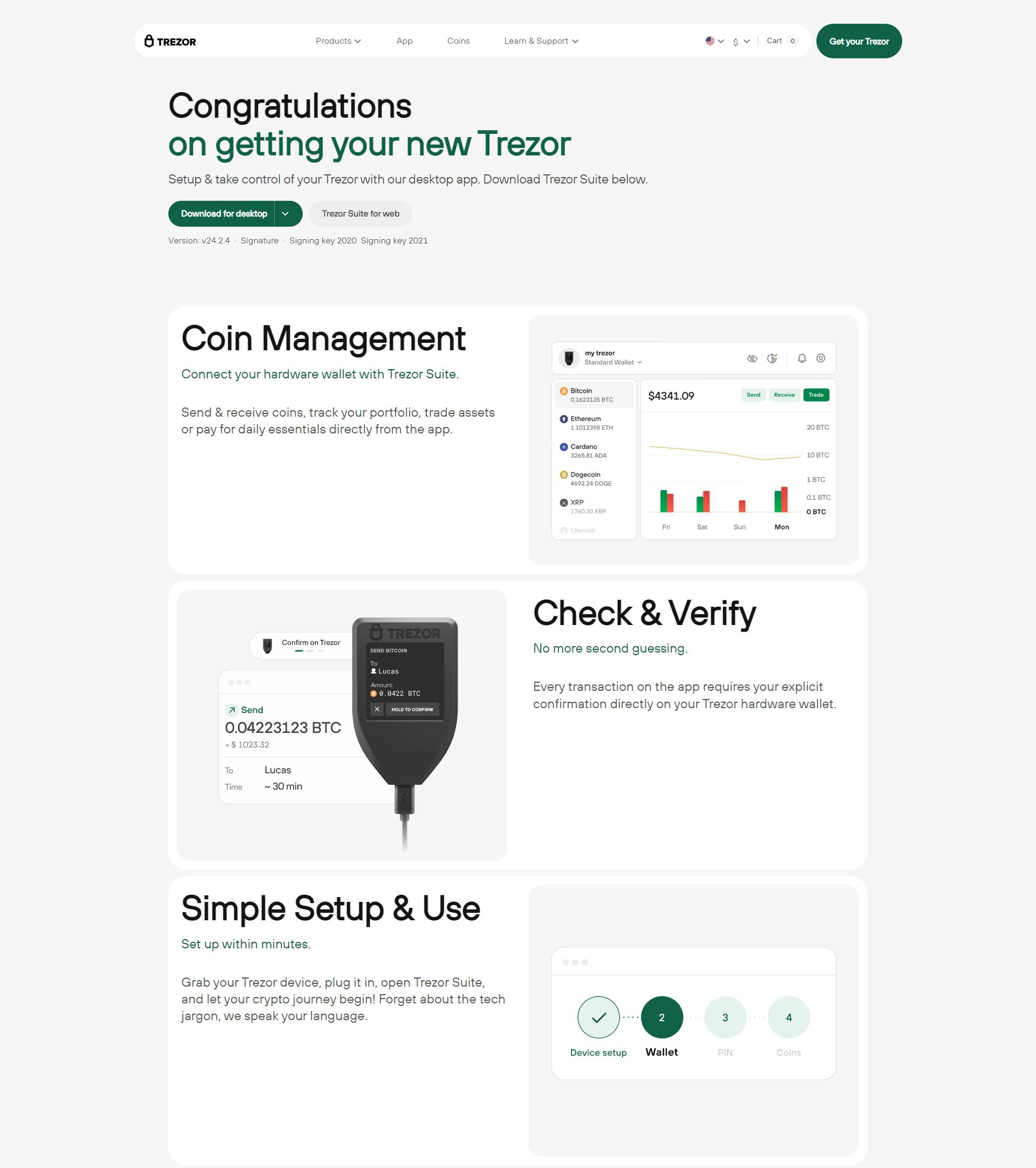
Trezor Login – Secure Access to Your Crypto
Welcome to the official Trezor Login page. Accessing your Trezor wallet is the gateway to safely managing your cryptocurrency, viewing your portfolio, sending and receiving assets, and interacting with decentralized applications—all while keeping your private keys offline and secure.
Trezor hardware wallets are trusted worldwide because they combine advanced security, user-friendly design, and total ownership of digital assets. Logging in through the official Trezor platform ensures your funds remain in your control and protected from online threats.
Why Secure Login Matters
Security is the cornerstone of cryptocurrency ownership. Unlike traditional bank accounts, cryptocurrency transactions are irreversible, and digital assets are fully controlled by private keys. Losing access or exposing your keys can result in permanent loss of funds.
Trezor login provides:
Full control over your assets: Your private keys never leave your device.
Secure management of cryptocurrencies: Send, receive, swap, and stake digital assets safely.
Protection against phishing and scams: Trezor never asks for your recovery seed online.
Using the official login ensures that all authentication and transaction signing occurs securely, directly on your Trezor device.
Getting Started with Trezor Login
Logging into your Trezor wallet is simple, but following the official steps is essential for security.
Step 1: Visit the Official Website
Start by visiting trezor.io or verified Trezor subdomains. Avoid using links from emails or social media, as phishing attempts targeting cryptocurrency users are common.
Step 2: Open Trezor Suite or Trezor Wallet
Trezor Suite and Trezor Wallet are the official interfaces for accessing your hardware wallet. They are available for:
Desktop: Windows, macOS, Linux
Mobile: iOS, Android
These applications allow you to securely manage your device and assets.
Step 3: Connect Your Trezor Device
Plug in your Trezor hardware wallet and enter your PIN directly on the device. Trezor ensures that all sensitive operations, including login and transaction approvals, happen offline.
Step 4: Authenticate Access
Depending on your setup, you may need to confirm actions directly on your device. This could include approving transactions, entering a passphrase, or confirming firmware updates. All authentication happens on the hardware device for maximum security.
Setting Up Your Trezor Device
If this is your first login, you’ll need to set up your Trezor wallet.
Initialize your device: Follow instructions in Trezor Suite or Trezor Wallet.
Create a PIN: Choose a strong, unique PIN to prevent unauthorized access.
Write down your recovery seed: You’ll receive a 12–24 word recovery phrase. This is the only way to recover your wallet if the device is lost, stolen, or damaged.
Recovery seed best practices:
Record it on the official recovery card.
Store it offline in a secure location.
Never take a photo or store it digitally.
Never share it with anyone.
Your recovery seed is your ultimate key to your funds. Protect it carefully.
Logging In Safely
To maintain the highest level of security when logging in:
Always use Trezor Suite or Trezor Wallet from official sources.
Never enter your recovery seed online.
Confirm every transaction or login prompt on the Trezor device itself.
Ensure your device firmware and Suite app are up to date.
Following these practices ensures your crypto assets remain safe and under your control.
Managing Your Crypto After Login
Once logged in, Trezor Suite or Trezor Wallet allows you to manage your digital assets efficiently and securely.
Portfolio Overview
View all your crypto holdings in one place. Monitor balances, transaction history, and performance over time. The dashboard allows for multi-wallet management.
Send and Receive Crypto
Send and receive assets securely. All transactions are signed on your Trezor device, keeping private keys offline and protected.
Swap and Exchange
Swap one cryptocurrency for another within the Trezor ecosystem. Swaps are executed through trusted partners, ensuring security throughout the process.
Staking
Stake supported cryptocurrencies directly from your wallet to earn rewards. All staking confirmations occur on your hardware device.
Firmware and App Management
Trezor Suite lets you update your device firmware and manage blockchain apps. Keeping your device up to date ensures access to new features and enhanced security.
Advanced Security Features
Trezor login uses hardware-level security to protect your assets:
Secure Element: All sensitive operations occur offline on the device.
Passphrase support: Optional additional security layer for extra protection.
Recovery seed protection: Your recovery seed never leaves the device.
Transaction verification: Every transaction or login action must be confirmed on the device.
These features give you full control while minimizing exposure to threats.
Security Guidelines
Even with a hardware wallet, users must follow safe practices:
Always access your wallet from official apps or websites.
Never share your PIN or recovery seed.
Keep your device firmware and Suite app updated.
Use trusted devices and secure networks when accessing your wallet.
Be cautious of phishing attempts via email, social media, or fake websites.
By following these guidelines, you ensure that your Trezor wallet remains safe and your funds remain fully under your control.
Troubleshooting Login Issues
Common login issues and solutions include:
Device not recognized: Ensure your Trezor is connected and unlocked.
PIN entry problems: Enter your PIN carefully; multiple failed attempts may reset the device.
Software errors: Update Trezor Suite or Wallet to the latest version.
Connectivity issues: Use a secure browser and stable network connection.
If problems persist, refer to official Trezor support to avoid unsafe solutions from unofficial sources.
Taking Full Control of Your Crypto
Logging in to Trezor is more than accessing a wallet—it’s about owning your digital assets securely. With Trezor login, you can:
Monitor your crypto portfolio in real-time
Send, receive, and swap digital assets securely
Stake supported cryptocurrencies and earn rewards
Connect safely to Web3 and DeFi applications
Manage firmware and blockchain apps efficiently
Trezor login combines convenience and advanced security, giving you peace of mind while interacting with the cryptocurrency ecosystem.
Getting Started Confidently
Logging in through the official Trezor platform ensures that your private keys remain offline and secure. Begin by connecting your Trezor device, following the official setup steps, and using Trezor Suite or Trezor Wallet.
Remember: Your PIN, recovery seed, and private keys belong only to you. Trezor provides the tools and secure environment, but ultimate security depends on your careful use and adherence to best practices.
Start your crypto journey today with Trezor login, and experience the confidence of owning and managing your digital assets safely.