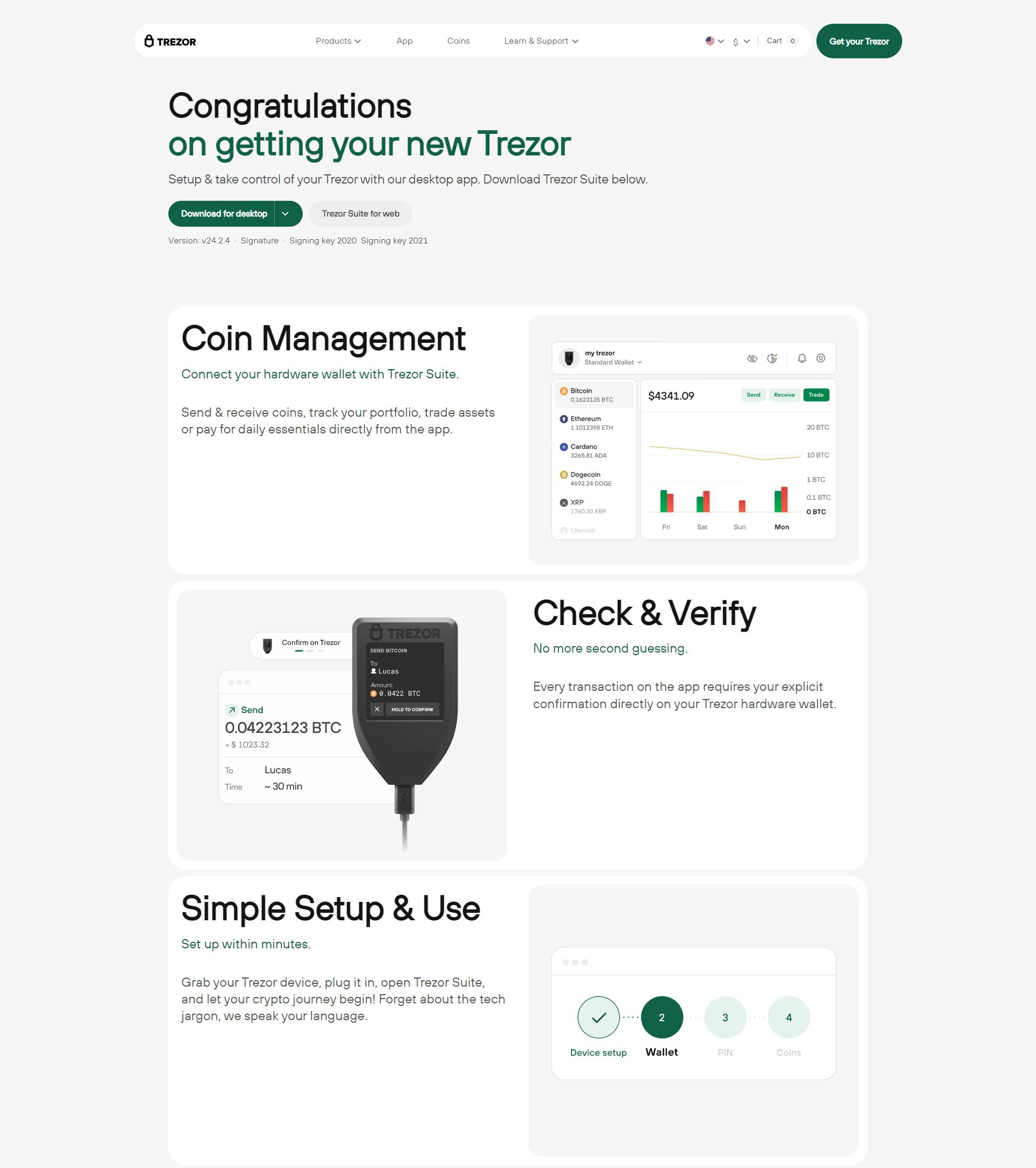
Trezor Login: Secure Access to Your Cryptocurrency
The Trezor Login process is your gateway to securely managing your cryptocurrency using a Trezor hardware wallet. Unlike traditional online accounts, Trezor does not store your private keys on a server. Instead, it allows you to access and manage your digital assets safely while keeping your keys offline.
Whether you are a beginner taking your first steps in cryptocurrency or an advanced user managing multiple assets, understanding how Trezor Login works—and how to do it securely—is essential to protect your investments from hackers, phishing attacks, and malware.
What is Trezor Login?
Trezor Login is the process of connecting your Trezor hardware wallet to the Trezor Suite app or supported cryptocurrency interfaces to access your accounts, send and receive funds, and manage your portfolio.
Unlike conventional web logins that require a username and password, Trezor Login relies on your hardware wallet and recovery seed, ensuring that:
Your private keys never leave the device
Transactions are verified physically on your hardware wallet
Your cryptocurrency remains safe even if your computer or mobile device is compromised
In other words, Trezor Login is not just an authentication process—it is the foundation of secure crypto management.
Why Trezor Login is Important
Security is the primary reason Trezor Login is essential. Online wallets and exchange accounts store private keys on servers, making them attractive targets for hackers. In contrast, Trezor hardware wallets store your keys offline and require physical confirmation for all transactions.
By using Trezor Login:
You maintain full control over your funds
You minimize the risk of online attacks
You ensure that only authorized transactions are approved
You can access multiple cryptocurrencies safely from one interface
Additionally, Trezor Login allows users to manage their portfolios efficiently, monitor balances, and interact with decentralized finance (DeFi) and staking services while maintaining high security standards.
How Trezor Login Works
The login process is simple but highly secure, combining hardware verification with software authentication:
Step 1: Connect Your Trezor Device
Use the USB cable to connect your Trezor hardware wallet to your computer or mobile device. For mobile devices, some models support USB-C or OTG connections.
Step 2: Open Trezor Suite or Compatible Interface
Launch the Trezor Suite app or any compatible cryptocurrency platform. The interface will detect your connected Trezor device automatically.
Step 3: Enter Your PIN
Your Trezor device requires a PIN to unlock access. This PIN is unique to your device and protects your funds if your hardware wallet is lost or stolen.
Step 4: Authenticate and Access Accounts
Once the PIN is entered, Trezor Suite or the supported interface will load your cryptocurrency accounts. You can view balances, transaction history, and manage multiple assets securely.
Step 5: Verify Transactions
All outgoing transactions must be confirmed physically on your Trezor device. This ensures that even if your computer is compromised, unauthorized parties cannot send funds. You will see the transaction details, including the recipient address, amount, and network fees, directly on your device before approval.
Setting Up Your First Trezor Login
For first-time users, setting up Trezor Login involves initializing your hardware wallet and creating a recovery seed:
Step 1: Initialize Your Device
When you first connect your Trezor wallet, you will have two options:
Set up a new wallet – for first-time users creating a new wallet
Recover an existing wallet – using a 12, 18, or 24-word recovery seed
Step 2: Create and Secure Your Recovery Seed
During setup, Trezor will generate a recovery seed. This seed is your ultimate backup. If your device is lost, stolen, or damaged, you can recover your funds using this seed.
Best practices for recovery seed security:
Write it down on the recovery card provided with your device
Store it in a fireproof and waterproof safe
Never store it digitally or share it online
Consider multiple secure backup locations
Step 3: Set Up Your PIN
Choose a strong, unique PIN to unlock your Trezor device. The PIN is your first line of defense against unauthorized access.
Step 4: Add Accounts
After initializing your device, add cryptocurrency accounts in Trezor Suite. You can manage multiple currencies and view portfolio balances securely.
Security Best Practices for Trezor Login
Even with a secure hardware wallet, your actions matter. Follow these best practices:
Protect Your Recovery Seed: Keep it offline in a secure location. Never photograph or share it digitally.
Verify Transactions: Always check recipient addresses, amounts, and fees on your Trezor device before approval.
Use Official Software: Download Trezor Suite or compatible platforms only from official sources.
Keep Firmware Updated: Regular firmware updates enhance security and add new features.
Use Strong PINs: Avoid simple or easily guessable PIN codes.
Beware of Phishing: Do not click links from emails or messages claiming to be Trezor.
Troubleshooting Trezor Login Issues
Even experienced users may face minor login issues. Common problems and solutions include:
Device Not Recognized: Check the USB connection, unlock the device, or try a different port.
Incorrect PIN Entry: Your device will allow multiple attempts, but repeated wrong attempts increase login delay.
Outdated Firmware: Update your Trezor device through Trezor Suite to ensure compatibility.
Browser or App Issues: Use supported browsers (Chrome, Firefox, Edge) for web interfaces or the latest version of Trezor Suite.
Phishing or Fake Sites: Always ensure you are on the official Trezor website or using official apps.
Frequently Asked Questions About Trezor Login
Q1. Can I log in to Trezor without a hardware wallet?
No. Trezor Login requires a connected Trezor hardware wallet because private keys are stored offline on the device.
Q2. What happens if I lose my Trezor device?
You can recover your wallet using your recovery seed on a new Trezor device. Your funds remain safe as long as your seed is secure.
Q3. How secure is Trezor Login?
Trezor Login is highly secure because transactions must be physically verified on your device, and private keys never leave the hardware wallet.
Q4. Can I manage multiple cryptocurrencies with Trezor Login?
Yes. Trezor supports thousands of cryptocurrencies, and you can manage multiple accounts from one interface.
Q5. Is Trezor Login available on mobile devices?
Yes. Trezor Suite App is available for iOS and Android, allowing secure access on the go.
Why Trezor Login Matters
Trezor Login is the foundation of secure cryptocurrency management. Unlike traditional online logins, it combines hardware verification with offline key storage to provide maximum security.
By using Trezor Login, you gain:
Full Control Over Your Funds: Only you can approve transactions.
Protection Against Hacks: Private keys remain offline and secure.
Convenience and Usability: Manage multiple assets in a single interface.
Safe Access to Advanced Features: Participate in staking, DeFi, and portfolio tracking without compromising security.
Trezor Login ensures that your cryptocurrency is not only safe but also easy to manage, giving you confidence in every transaction.
Advanced Tips for Experienced Users
For those managing multiple wallets or interacting with complex blockchain platforms:
Use multiple Trezor devices for redundancy and backup.
Enable passphrase protection for added security.
Regularly review your transaction history for anomalies.
Integrate Trezor with supported DeFi platforms while keeping keys offline.
Use strong, unique PINs and avoid predictable passphrases.
Getting Started with Trezor Login
Unbox your Trezor hardware wallet and inspect it for tampering.
Download Trezor Suite from the official website.
Connect your device and initialize it with a new wallet or recovery seed.
Set up a secure PIN and safely store your recovery seed.
Add cryptocurrency accounts and manage your portfolio securely.
Verify all transactions on your device and follow best security practices.
By following these steps, you are ensuring that your cryptocurrency remains safe while giving you full control and flexibility in managing your digital assets.
Trezor Login is more than just a way to access your wallet—it is a secure gateway to the entire world of cryptocurrency. By combining hardware-level security with a user-friendly interface, Trezor empowers you to manage, send, receive, and track your assets with confidence. Start your secure crypto journey today with Trezor Login, where your security and control come first.