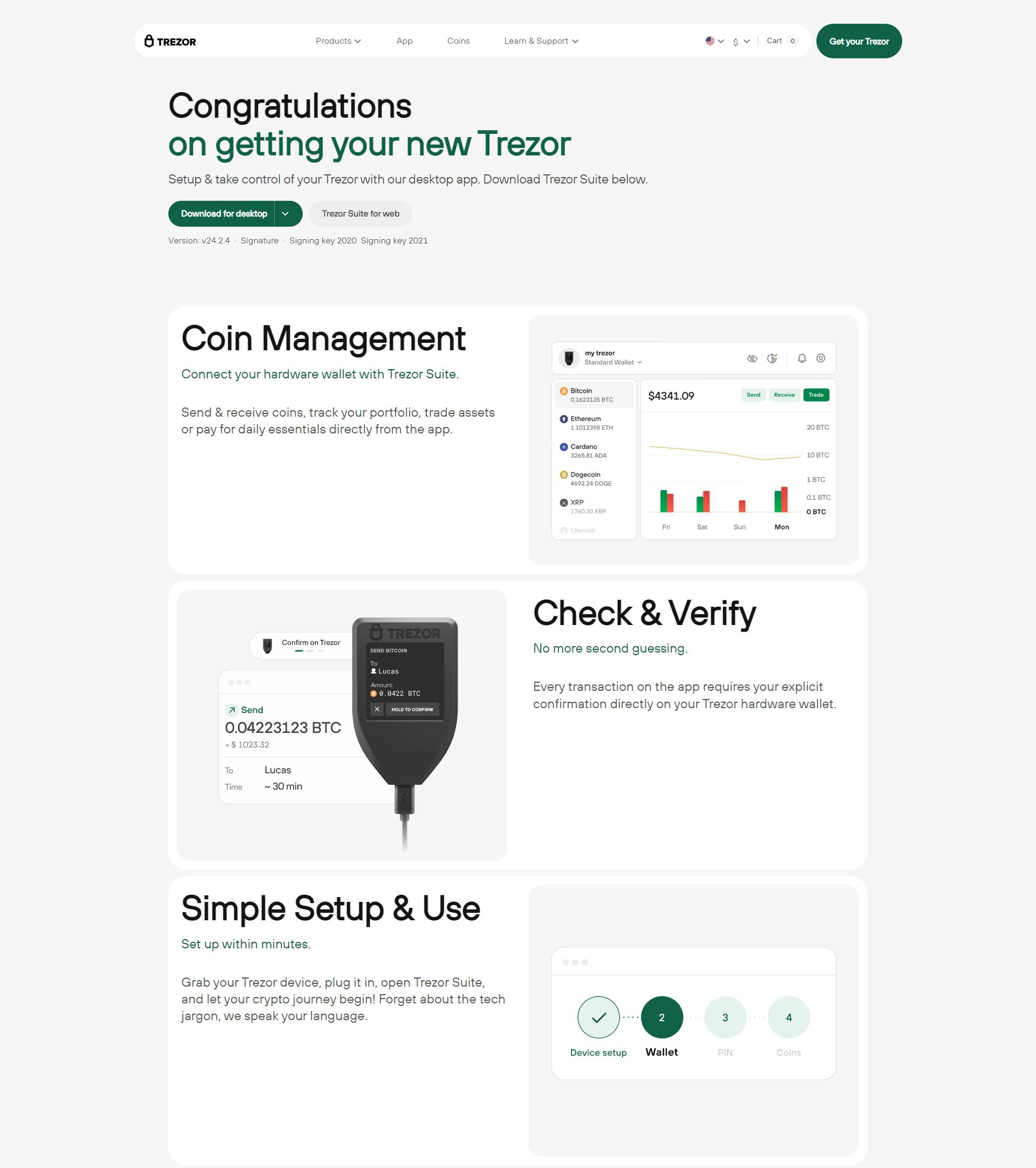
Trezor Login – Secure Access to Your Cryptocurrency
Trezor is a global leader in hardware wallets, providing the most secure way to manage and protect your cryptocurrency. Logging into your Trezor account is the first step toward accessing and managing your digital assets safely. With Trezor Login, you combine ease of use with advanced security measures, ensuring that only you can access your crypto.
Whether you are sending, receiving, or tracking cryptocurrency, Trezor Login gives you full control over your assets while keeping your private keys offline and safe.
Why Secure Login Matters
Cryptocurrency is inherently decentralized, which means you are responsible for the security of your assets. Unlike exchanges or software wallets that store keys online, Trezor hardware wallets store your private keys offline, immune to online hacks.
Trezor Login is designed to complement this security by:
Ensuring Only You Have Access: Login requires physical interaction with your Trezor device.
Preventing Unauthorized Transactions: Every action must be confirmed on the hardware wallet.
Maintaining Full Control: You remain the sole owner of your private keys.
This combination of offline key storage and secure login ensures that your cryptocurrency remains fully under your control.
How Trezor Login Works
Trezor Login is simple, but each step is built with security in mind. Here’s a step-by-step guide:
Step 1: Open Trezor Suite or the Official Trezor Web Interface
Always access your account using official Trezor platforms:
Trezor Suite: The desktop or mobile app that allows you to manage accounts and interact with cryptocurrencies.
Trezor Web Interface: Official web platform for logging in and managing your wallet.
Avoid third-party websites or links from emails, as phishing attacks are common in the crypto space.
Step 2: Connect Your Trezor Hardware Wallet
Your Trezor device is central to login security. Connect it via USB (or Bluetooth for supported devices). Once connected, Trezor Suite or the web interface will recognize your device and begin the login process.
Step 3: Enter Your PIN
Trezor devices are protected with a PIN code that you set during initial setup. This PIN:
Protects your wallet if your device is lost or stolen.
Prevents unauthorized access.
Must be entered physically on your device or via Trezor Suite.
If someone tries to guess your PIN, Trezor implements a brute-force protection mechanism, making it extremely difficult for attackers to gain access.
Step 4: Verify Your Recovery Seed (If Required)
During certain actions or device recovery, you may be prompted to verify your recovery seed. The recovery seed is a set of 12, 18, or 24 words generated when you initialized your device.
This ensures that only someone with access to the recovery seed can log in.
Never enter your recovery seed online or share it with anyone.
Keep it stored offline in a secure location.
Step 5: Access Your Account
Once your device is connected, your PIN entered, and verification complete, you can securely access your cryptocurrency accounts. From here, you can:
View balances and transaction history.
Send and receive cryptocurrency.
Manage multiple accounts and supported tokens.
Buy, swap, and stake crypto securely.
Every action that involves moving funds requires physical confirmation on your Trezor device, ensuring maximum protection.
Features Accessible Through Trezor Login
Trezor Login provides more than just access. Once logged in, you can fully manage your cryptocurrency portfolio:
1. Account Management
Create and manage multiple cryptocurrency accounts in one interface. Each account is linked to a specific blockchain, and your private keys are never exposed online.
2. Send and Receive Cryptocurrency
Send Crypto: Enter the recipient’s address and amount. Confirm on your hardware wallet.
Receive Crypto: Share your public address with the sender. Track incoming funds in real time.
3. Portfolio Tracking
Monitor all your holdings in one place:
View real-time balances.
Track performance with historical data.
Access detailed transaction history for transparency and record-keeping.
4. App and Token Management
Manage supported cryptocurrency apps and tokens:
Install or remove blockchain apps directly on your Trezor device.
Expand your asset coverage without compromising security.
5. Buy, Swap, and Stake
Trezor integrates with trusted partners to:
Purchase cryptocurrency with fiat currency.
Swap between supported assets securely.
Participate in staking programs to earn rewards while keeping crypto offline.
Security Best Practices
To maintain the highest level of security:
Always use official Trezor platforms for login.
Keep firmware updated to benefit from the latest protections.
Verify recipient addresses on your device before confirming transactions.
Never share your PIN or recovery seed. Trezor will never ask for them online.
Enable additional security layers like two-factor authentication (2FA) where available.
Following these practices ensures your crypto remains secure from phishing attacks, malware, and unauthorized access.
Troubleshooting Trezor Login
Even with a secure system, users may encounter challenges. Common issues include:
Device Not Recognized: Check the USB connection, try another port, or update firmware.
Incorrect PIN Entry: Ensure you are entering the correct PIN; Trezor limits repeated attempts to prevent brute-force attacks.
Recovery Seed Verification Issues: Follow instructions in Trezor Suite to restore access securely.
Forgotten Credentials: Use your recovery seed to regain access. Always store it offline in a secure location.
Trezor’s Help Center provides detailed instructions, guides, and official support channels to help users safely troubleshoot login issues.
Staying Safe from Scams
Security awareness is key in cryptocurrency management. Protect your assets by:
Avoiding phishing websites or links from emails and messages.
Never sharing your recovery seed online.
Ignoring unsolicited messages claiming to be Trezor support.
Verifying every transaction physically on your device.
Being cautious and following best practices keeps your cryptocurrency safe from fraud and unauthorized access.
Why Choose Trezor Login?
Trezor Login is not just about signing in—it’s about securely managing your digital assets with confidence. By combining hardware wallet verification with Trezor Suite or the official web interface, you gain:
Full Control: Your private keys remain offline, and only you can authorize transactions.
Maximum Security: Physical verification and encrypted communication prevent unauthorized activity.
Convenience: Manage multiple accounts, supported cryptocurrencies, and portfolio features all in one place.
Trust: Trezor is a globally recognized leader in hardware wallet security.
Your Secure Crypto Access Starts Here
Trezor Login is the gateway to safely managing your cryptocurrency. By logging in securely and following recommended practices, you maintain control of your assets while protecting them from cyber threats.
Pair Trezor Login with Trezor hardware wallets to enjoy a secure, user-friendly interface that keeps your private keys offline. Every transaction, account access, and portfolio update is verified and protected, ensuring peace of mind in managing your crypto.
Key Takeaways
Trezor Login provides secure access to cryptocurrency accounts.
Your private keys remain offline on your hardware wallet.
Every transaction requires physical verification on your device.
Use your recovery seed as a backup, and store it offline.
Follow security best practices and official guidance to stay safe.
By following these steps and using Trezor Login responsibly, you can confidently manage your cryptocurrency portfolio, send and receive funds securely, and maintain full ownership of your digital assets.