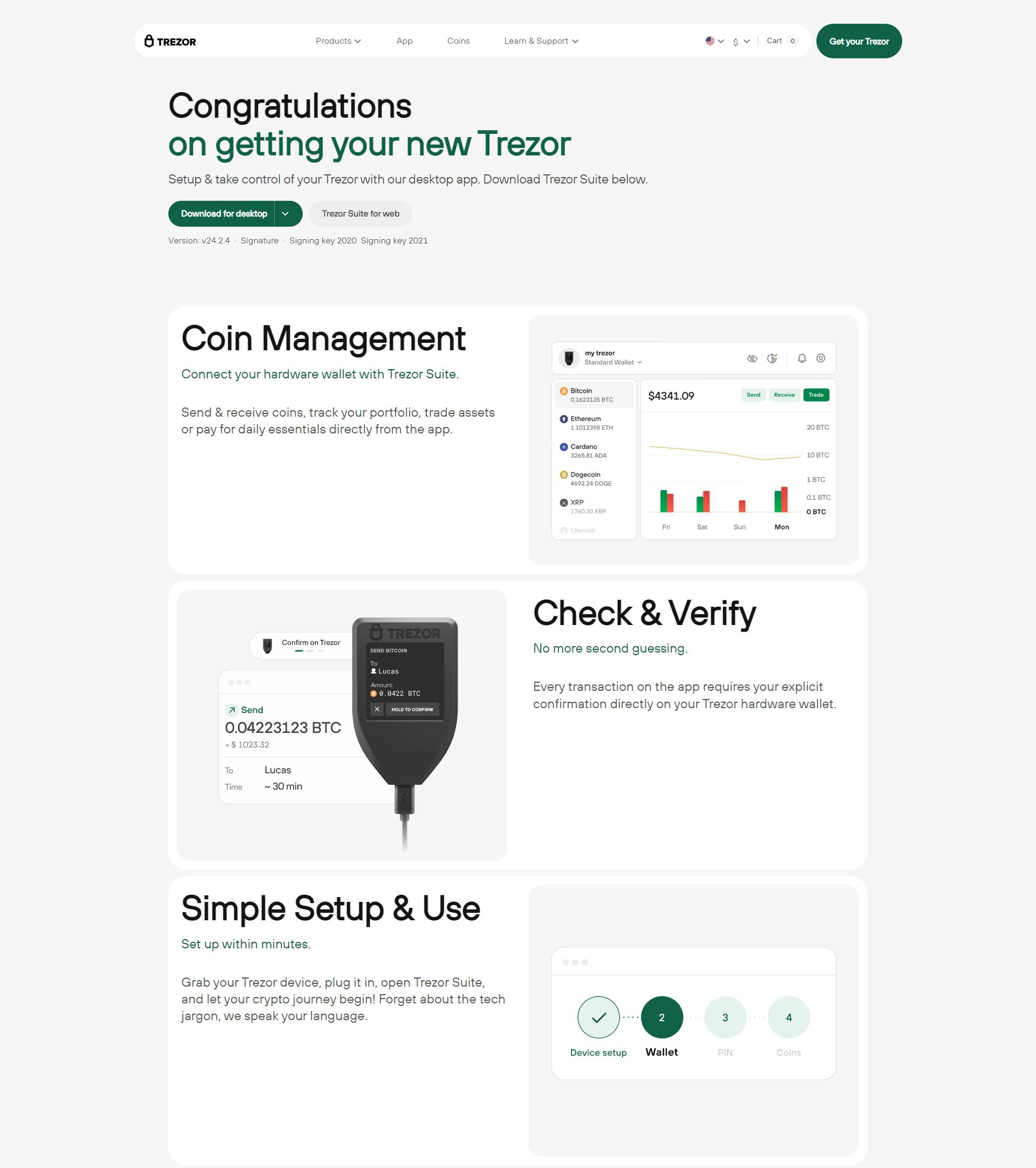
Welcome to Trezor Login – Secure Access to Your Cryptocurrency
Trezor Login is your official gateway to accessing the Trezor ecosystem safely and efficiently. With Trezor Login, you can manage your cryptocurrency accounts, interact with Trezor Suite, and perform transactions while keeping your private keys completely offline.
Trezor has been a pioneer in cryptocurrency security, providing hardware wallets that protect digital assets from malware, phishing attacks, and unauthorized access. Logging in through Trezor ensures that your funds remain secure and that your sensitive information is always protected.
Whether you are new to cryptocurrencies or an experienced investor, understanding Trezor Login is essential for safely managing your digital assets.
Why Trezor Login Is Important
Cryptocurrency security starts with proper access management. Trezor Login is more than a standard username-and-password system. It connects your Trezor hardware wallet to the Trezor Suite app and online services, ensuring that private keys never leave the device.
Unlike traditional software wallets or online exchanges, Trezor’s hardware-first security model guarantees that your assets cannot be accessed by malware or hackers on your computer. When you log in through Trezor, all sensitive operations—like signing transactions—are verified directly on your hardware wallet.
Trezor Login also provides secure access to services like:
Trezor Suite – for managing cryptocurrency accounts and portfolios
Device management – for setting up, updating, or recovering your hardware wallet
Educational resources and official support – for guidance on using Trezor safely
This secure login system is a key part of maintaining control and ownership of your digital assets.
Getting Started with Trezor Login
Accessing your Trezor account is straightforward, but following official instructions ensures maximum security:
Visit the Official Trezor Login Page
Always start at the official Trezor website. Avoid clicking on login links from emails, messages, or social media, as phishing attempts are common.Enter Your Credentials
Use the email address linked to your Trezor account and your chosen password. Ensure your password is strong, unique, and not reused across multiple platforms.Connect Your Trezor Hardware Wallet
Trezor Login requires verification through your hardware device. Plug your Trezor wallet into your computer or mobile device, and follow the prompts to unlock it using your PIN code.Two-Factor Authentication (2FA)
If enabled, you will be prompted to enter a verification code from an authenticator app or another secondary method. This adds an essential layer of protection against unauthorized access.Access Trezor Services
After successfully logging in, you can access Trezor Suite, manage accounts, initiate transactions, and explore advanced features while keeping your private keys securely offline.
Following these steps carefully ensures that your login process remains safe and secure.
Security Features of Trezor Login
Trezor Login is built to provide maximum security for your digital assets. Some of its key security features include:
Hardware Wallet Verification – Your private keys never leave your Trezor device, and all transactions are confirmed on the hardware.
PIN and Passphrase Protection – Access to your device and account is secured with a PIN, and an optional passphrase provides an additional layer of security.
Recovery Seed Backup – Your recovery seed allows you to restore access if your device is lost or damaged. Keep it offline and secure.
Two-Factor Authentication (2FA) – Adds an extra layer of protection to prevent unauthorized access.
Anti-Phishing Measures – Trezor Login ensures you only interact with verified services and official websites.
These features make Trezor Login one of the most secure ways to access your cryptocurrency accounts.
Managing Your Trezor Account
Once logged in, Trezor Login gives you access to a range of tools and features:
Profile Management – Update your account information, email, and preferences.
Device Management – Register new devices, update firmware, and manage existing hardware wallets.
Portfolio Overview – Monitor balances and transactions across all supported cryptocurrencies.
Transaction Management – Initiate, verify, and track transactions securely through your hardware wallet.
Educational Resources – Access tutorials, guides, and security tips for safe cryptocurrency management.
By centralizing these functions, Trezor Login simplifies account management while maintaining a high level of security.
Multi-Factor Authentication for Extra Protection
Trezor strongly recommends enabling two-factor authentication (2FA) for your account. 2FA requires a second form of verification in addition to your password, usually a code from an authenticator app.
The advantages of 2FA include:
Enhanced Security – Even if your password is compromised, unauthorized users cannot access your account without the second verification factor.
Protection Against Phishing – 2FA adds a barrier against common online attacks targeting login credentials.
Peace of Mind – You can access your accounts confidently, knowing that multiple layers of protection safeguard your assets.
Setting up 2FA through Trezor Login is simple and provides a critical layer of defense for your cryptocurrency accounts.
Best Practices for Using Trezor Login
To maximize security and maintain control over your accounts, follow these best practices:
Use Strong, Unique Passwords – Avoid reusing passwords from other services.
Enable Two-Factor Authentication – Protect your account with an additional verification step.
Never Share Recovery Seeds or PINs – Your recovery seed and PIN are private and should never be shared.
Verify URLs Carefully – Always access Trezor Login through the official website.
Monitor Account Activity – Regularly review transactions and alerts for any suspicious activity.
Keep Firmware and Software Updated – Maintain the latest security updates for your Trezor device and software.
By following these practices, you ensure that your account remains secure and that your digital assets are protected from unauthorized access.
Troubleshooting Common Login Issues
Even with secure systems, users may occasionally face login challenges. Some common issues and solutions include:
Forgotten Password – Use the official password recovery process to reset your credentials safely.
Device Not Recognized – Ensure your Trezor device is connected properly, update firmware, and check USB or mobile connections.
2FA Problems – Ensure your authenticator app is synchronized correctly and that your device time settings are accurate.
Account Lockout – Contact Trezor official support if you are unable to access your account after multiple attempts.
Official support resources ensure that any login issues are resolved safely, without compromising account security.
Why Trezor Login Is Essential
Trezor Login is a crucial component of the Trezor ecosystem. It bridges the gap between convenience and security, allowing users to manage digital assets efficiently while keeping private keys protected offline.
By requiring hardware wallet verification and supporting multi-factor authentication, Trezor Login ensures that your cryptocurrency remains secure against unauthorized access, phishing, and malware attacks.
Whether you are managing a single wallet or multiple accounts, Trezor Login provides a secure and reliable foundation for cryptocurrency management.
Start Using Trezor Login Today
Trezor Login is your official gateway to safely managing digital assets. By following the secure login process, connecting your Trezor device, and enabling two-factor authentication, you can access Trezor Suite and other services with confidence.
With Trezor Login, you can:
Securely access your cryptocurrency accounts
Monitor balances and transactions across multiple wallets
Manage Trezor devices and update firmware
Interact with Trezor Suite for portfolio management and staking
Access official resources, guides, and support
Start today with Trezor Login and take control of your digital assets with the confidence that your private keys and funds are protected by one of the most trusted hardware wallet solutions in the cryptocurrency world.